ITSG Blog

Ansible Unlocking Advanced Automation Techniques
If you’ve already got the basics of Ansible down, it’s time to take your skills to the next level. Building on what we’ve covered in
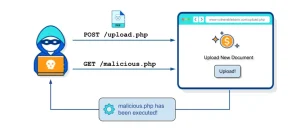
File Upload Attack
File upload vulnerabilities represent one of the most critical security risks faced by web applications. As businesses increasingly rely on user generated content and file

Linux VPN Connection Issues
One of the common issues faced by Linux users when using a VPN is the inability to connect orfrequent disconnections. This issue is often caused

Email injection
As someone who thrives on exploring the intricacies of security vulnerabilities, I believe in sharing the techniques and knowledge I use in real-world projects can

Store XSS On Cryptocurrency Website
Sometimes vulnerability is in the simplest things that cannot be seen…I haven’t felt like working much lately. I’ve mostly been studying and doing a little

RECON (Reconnaissance)
RECON or Reconnaissance in web security is the first and one of the most important stages of security assessment. This stage includes gathering information about
CORS VULNERABILITY
The CORS vulnerability, which stands for Cross-origin resource sharing, is one of the most dangerous vulnerabilities, in the sense that an intruder can obtain various
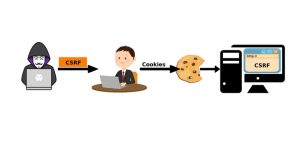
CSRF VULNERABILITY
A CSRF attack usually targets state-changing actions like deleting records, changing passwords, buying products, or sending messages. Hackers often use social engineering to send malicious
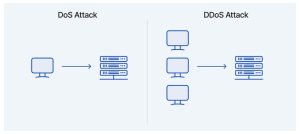
DOS & DDOS ATTACK
In a Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attack, a hacker or intruder sends a large number of malicious and half-open requests to a server

Cisco Router and Switch Password Recovery
Password recovery on Cisco routers and switches can disrupt even the most organized networks. This guide equips you with proven methods to recover access efficiently,

CloudLinux
Advanced and sophisticated attacks now being deployed by anonymous individuals havesignificantly increased the importance of security in the web and hosting spaces. Given theplethora of
Information Disclosure + XSS on Android APP
I believe the security is a complex and very important process. Due to the lack of permission,the name of the application is not mentioned, and

Installation & Introduction of Ansible -The Magic Automation
Imagine a world where managing complex Network & OS configurations is as simple aswriting a few lines of code. Ansible is a game-changer in the

Ansible Mastering Its Structure for Effective Automation
Ansible Mastering Its Structure for Effective Automation In this article, we will delve into the structure of Ansible, examining key components such as Playbooks and
Ansible The Art of Configuring Cisco Switches with Ansible
Ansible is a powerful automation tool that simplifies the management and configuration of network devices. Automating Cisco switch configurations with Ansible not only saves time
